| NEW - Social Media Apps - What Parents Need to Know |
Thanks for your #MackPics!
Keeping a Safe App Environment for Tweens (and more
great info) |
|
|
We hope that you have enjoyed our daily #InstaSmart Tweets
and helpful tips on protecting yourself online and when
using social media.
Join
our new campaign to apply what we’ve learned!
Please
use the hashtag
#MACKpics, to help
us promote Commack Pride.
Here’s how: Please submit
positive photos capturing community pride and school
sponsored events by tagging your pictures on Instagram,
Twitter, or Facebook using
#MACKpics and
your photo may be selected for a photo montage, on
the Commack Website, or even in the annual Commack Schools
Calendar!
|
Who are
you really talking with?
Anyone can open an email
account and create a false identity. A good practice is:
If you've never met the person in real life, don't provide information that could help them find you.
The FBI estimates there are 750,000 child predators online
at any one time (http://wjla.com/features/7-on-your-side/stranger-in-the-console-113707)
which is scary! so be especially careful with online
gaming systems that may open the door to an internet
predator looking to find and meet up with you.
Disable the camera/video feed in online gaming systems - in
Xbox, PlayStation, Wii, Kinect, and other online
game systems, even in your phone.
http://www.nbcchicago.com/investigations/unit-5-video-games-internet-devices-child-predators-173429241.html

|
Privacy,
privacy, privacy!!!
We've passed on a lot of tips about staying secure online in the last two weeks. There are settings in your web browsers that prevent tracking the websites you visit, the purchases you make, and even your web searches (try the DuckDuckGo search engine).
 Cookies are small text files that are stored on your computer's browser directory. They create a trail of where you've been, your log on information, and can be accessed by a web server or a client computer. They can be used by a third party without your knowledge. Learn to manage cookies, and keep security settings high
and privacy settings turned on. Cookies are small text files that are stored on your computer's browser directory. They create a trail of where you've been, your log on information, and can be accessed by a web server or a client computer. They can be used by a third party without your knowledge. Learn to manage cookies, and keep security settings high
and privacy settings turned on.
|
What are Cookies?
https://kb.iu.edu/d/agwm
Browser Security Settings: You will need to determine which browser you are using first (Help, About on the menu bar) Here's a general article:
https://www.veracode.com/blog/2013/03/browser-security-settings-for-chrome-firefox-and-internet-explorer
How to Remove Embarrasing Photos from Social Media:
https://www.seoinc.com/seo-blog/how-to-remove-embarrassing-photos-from-social-media/
|
Often your online friends
are not your real friends, so limit the number of
people who can read and comment on your posts.
People you don't know are strangers - remember what your mother said about speaking to strangers!
How many online friends do you have? Really?
|
Do you have strong passwords? Keep your devices protected
- Don't share your passwords - even with your best friend.
- Change your
passwords often.
- Don't use the same passwords for your important accounts.
- Always sign out of your email account, don't just close the window.
- Password
protect your phone, your computer, and all your
devices.
|
 |
Finding it hard to keep track of them all? Here's one suggestion - put them all in a spreadsheet and then password protect your spreadsheet. Then you only have to remember one password.
You can also try one of the online password generating
services, but choose with care!
http://www.google.com/goodtoknow/online-safety/passwords
http://krebsonsecurity.com/password-dos-and-donts/
************************************************************************** |
Stay away from location networking – I know where
you are!
You're providing a BIG piece of the puzzle to strangers when you post something and your location is turned 'on' in your cell phone or other device. Foursquare, Instagram, BuzzMob, the list is endless.
Location-based services can be one of the most dangerous
features provided by social networking sites. It exposes the
profile user’s location and whereabouts. The service also
has a feature that allows users to tag who they are with at
any given time. While it can be fun to share your location
with friends and family, it can also increase your
vulnerability, potentially opening you up to being robbed,
sexually assaulted, or worse. Predators can use this tool to
track your movements and determine when you are alone or
when you are not at home.
Geolocation, Tweeters beware!
|
Find
a balance, have screen-free time
Take a break from technology, and enjoy your family, pets, friends,
and the
outdoors! Unplug and play!
Did you know?
Children between the ages of 8 and 18 use media devices an
average of 7 1/2 hours a day
U.S. Adults spend 11 hours per day with digital media
Even babies and toddlers are at risk for screen-time
overload
Tips for reducing screen time:
-
Ignore your cell phone's texts and calls and focus on having a real conversation with whoever you're with.
-
Eat a family meal
together, and turn off the TV - no electronic
devices either
-
You'll get more sleep, reduce stress, and even lose weight if you don't use devices for two hours before bedtime.
|
Article:
Limit screen time for healthier kids
|
Know what not to share. Keep personal info private.

You wouldn't open your front door to a stranger and let them look around your home, would you? Don't put information online about you that could lead an online predator to your door or into your bank account.
Here's some tips to keep a lock on your info:
http://techland.time.com/2013/07/24/11-simple-ways-to-protect-your-privacy/
http://enlightenme.com/top-10-ways-to-keep-your-personal-information-safe-on-the-internet/
http://www.reputation.com/blog/privacy/top-ten-reasons-keep-your-personal-information-private
|
When
in doubt, throw it out:
You've won $5,000! Really? Links in email, tweets, posts, and online advertising are often the way cybercriminals compromise your computer. If it looks suspicious, (sometimes even if you know the source/sender), it’s best to delete - or if appropriate - mark as junk email. NEVER open attachments with the file extension .exe.
Better to be safe than sorry. Use the Delete key! Protect your
computer with antivirus software, too.
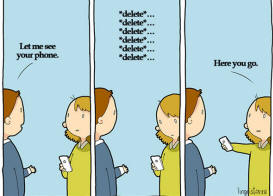 |
If you have been sent something inappropriate, delete it. Don't be in possession of something that could get you in trouble. |
|
 Don't announce your empty house! Don't announce your empty house!
You worry about identity theft when making purchases online - but do you realize that by posting vacation pictures, your itinerary, and "checking in" your location via social media, it can lead to your home being burglarized? Burglars use social media, too.
Checking in at the airport or your hotel might seem like a fun way to let friends and family know you're on vacation, but burglars are also combing through social media looking for easy targets. These criminals only need a rough idea of where you live and access to Google Street View to start casing your home.
Some Tips:
-
Turn off location
information on social media apps
-
Don't share your address
-
Only share
information with friends (not friends of
friends!)
-
Turn off EXIF
meta-data contained in image files which
contains GPS locations
-
Refrain from posting pictures while you're on vacation - wait til you get home
- Don't EVER post a picture of your boarding pass. The QR code on it contains loads of info about you!
|
http://www.ibtimes.com/how-burglars-use-facebook-target-vacationing-homeowners-1341325
|
Once posted,
always posted
THINK Before You INK!
What is your digital footprint? Think about this: Every child born today has an online dossier. Thanks to Facebook, there may even be data from before birth. Digital footprints are not washed away as footprints in the sand are. The next big wave won't erase them. Once you put it out there, it is there
FOREVER!
Search engines can find
everything posted about you, and so can any random person in
the world.
So,
create your own digital tattoo/footprint. Choose what to
share on social media. Establish a positive online presence.
YOU can be in control to a certain extent.
Ask yourself...who is going to see this message/picture?
If the answer was EVERYONE, would you still send/post it?
|
|
 If you wouldn't say it to someone's face... If you wouldn't say it to someone's face...
There are grave consequences to cyberbullying.
Kids are often quiet about the hurt they are feeling
and it can push some
kids to their limits.
You don’t have to participate in online
bullying
to fit in with your
peers. Most teens don’t find cruelty to be cool.
 BREAK THE CYCLE BREAK THE CYCLE
Take the pledge to NOT participate in cyber
bullying
Don’t respond to, or forward mean or inappropriate
pictures/messages
Tell an adult who can help

|
Think before you hit the SEND button!
 Social
Media Etiquette Social
Media Etiquette
"Remember your manners," we are cautioned. Is that old fashioned advice? Not according to Forbes and the New York Times (see links below).
Ask yourself a few questions
before you post or send an email:
- Is my message
offensive?
- Will my post
hurt anyone?
- Does it violate anyone's privacy?
|
Altho proper spelling seems 2 B slipping when using social media, that's not true when sending an email. Emails are a different animal. An email can be forwarded to an unlimited number of people. Reread an email before you send it. Your "tone" is based on your words, so use words carefully. And remember, emails are frequently archived for years and years. Once you hit "Send" it's gone.
For more info:
Great VIDEO: Think Before You Post -
https://www.youtube.com/watch?feature=player_embedded&v=Asahg03unyI
Social Media Etiquette:
http://www.forbes.com/sites/ilyapozin/2013/01/09/social-media-etiquette-12-step-checklist/
Email Etiquette:
http://www.nytimes.com/2012/04/21/your-money/what-to-think-about-before-you-hit-send.html?mwrsm=Email&_r=0
Email Checklist:
http://sethgodin.typepad.com/seths_blog/2008/06/email-checklist.html
************************************************************************** |
What
does your digital tattoo say about you?
Find out!
Google your name and see what pops up about you.
-
Is your digital tattoo a true reflection of
who you are?
- Does it represent you in a positive way?
- How can it affect your college, career, and
relationships?
Questions you should ask
yourself before posting online:
- Would I want my...fill in the blank (teachers, parents,
employer, friends) to see this?
- Will
this information reflect well on me a year from now?
Five years from now?
- Who
might view or purchase this information about me?
- Are
there some details about my life I would like to keep
personal?
- What
conclusions might others form with my information?
Adapted from:
www.athinline.org
Digital Tattoos are harder to erase than an ink tattoo!
Be careful what you post!
Your Online Life, permanent as a tattoo - Video
|
|
Protect your online presence!
You think you’re safe….you trust you set
it all up correctly….but are you really protecting
yourself and your identity when you use social
media?
Protect
yourself with these STOP. THINK. CONNECT. tips:
·
Keep a clean machine:
Having the latest security software, web browser,
and operating system on your cellphone, computer, or
tablet are the best defenses against viruses,
malware, and other online threats.
·
Own your online presence: When
applicable, set the privacy and security settings on
websites to your comfort level for information
sharing. It’s ok to limit how you share information.
·
Make passwords long and strong:
Combine capital and lowercase letters with numbers
and symbols to create a more secure password.
·
Unique account, unique password:
Separate passwords for every account helps to thwart
cybercriminals.
·
To avoid giving away email addresses of your friends, do
not allow social networking services to scan your
email address book. When you join a new social network, you might receive an offer to enter your email address and password to find out if your contacts are on the network. The site might use this information to send email messages to everyone in your contact list or even everyone you've ever sent an email message to with that email address. Social networking sites should explain that they're going to do this, but some do not.
·
Choose your social network carefully.
Evaluate the site that you plan to use and make sure
you understand the privacy policy. Find out if the
site monitors content that people post. You will be
providing personal information to this website, so
use the same criteria that you would to select a
site where you enter your credit card.
See more at:
https://www.staysafeonline.org/stay-safe-online/protect-your-personal-information/social-networks#sthash.1MD2TTBl.dpuf
http://www.microsoft.com/security/online-privacy/social-networking.aspx
Protect
Yourself
- Use privacy settings
- Use your email wisely
- Don't talk to strangers online, and be smart with instant messaging (IM) programs
- Don't share personal or private information online
(Your name, school name, home address, phone numbers,
photos)
|
|
Are you Social Media Savvy?
Follow Commack School District's daily #InstaSmart tweets with the hashtags #InstaSmart to learn the ins and outs and the dos and don'ts of social media.
TWITTER - THE BASICS:
Do you have a Twitter
account?
To follow us @CommackSchools, sign up for an account at
www.twitter.com
Q&As for Today - What's a Hashtag?
A hastag is a word or
phrase preceded by a hashtag symbol (#) that is used to
identify messages on a specific topic. The hashtag make it
easier for users to find messages with a specific theme or
content. Using this symbol is another way of grouping what a
tweet is about with others that are talking about the same
thing.
What's a Tweet?
When you post something, it's a Tweet. Messages are limited to 140 characters. That includes letters and spaces.
Quick Twitter Tutorial...The symbols below are used on Twitter.
 |
Use the back arrow button to reply to a Tweet or
message that was posted. |
 |
Use the double arrows to 'retweet' or repost something someone else has said. |
 |
Clicking the star means you like ('favorite') the Tweet or message. |
 |
The three dots mean that you can copy the link to
the tweet. |
More help:
Getting started with Twitter |